How to Enhance DNS Privacy with DoT and DoH
The Domain Name System (DNS) guides us through the vast expanse of the internet. It is the unsung hero, translating human-readable domain names into the machine-readable IP addresses that our devices understand. But what happens when this essential process is not as private as we would like it to be? The implications for security, privacy, and even human rights can be profound.
The Risks of Plaintext DNS Queries
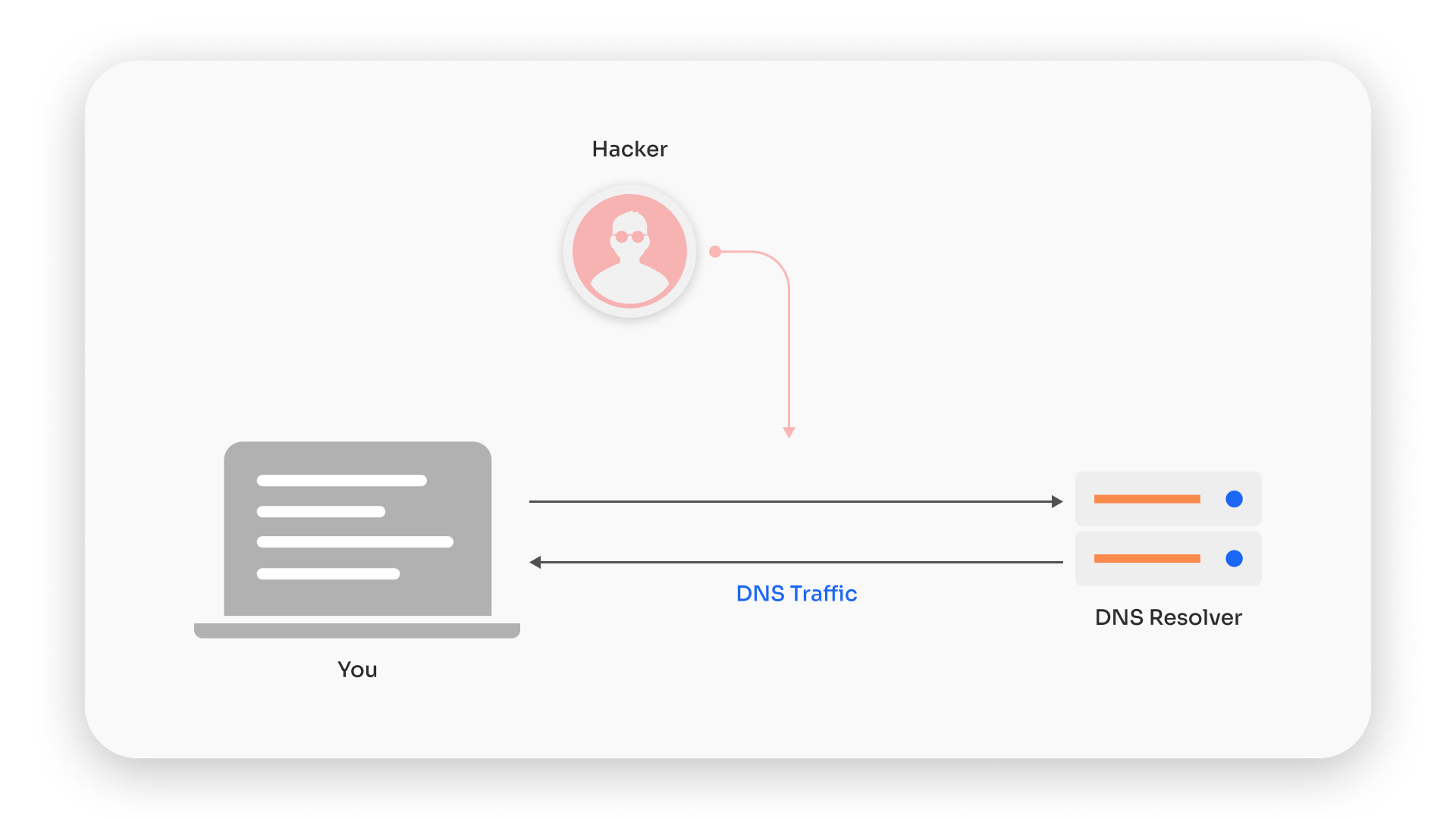
By default, DNS queries—the questions your computer asks to find the address of a website—are sent in plaintext. This means they are as open to prying eyes as a conversation in a crowded café. Whether it is a network administrator, an Internet Service Provider (ISP), or a more nefarious actor, anyone with the right tools can eavesdrop on these conversations. It is like announcing your destination aloud before stepping into a secret passage. The risks of doing this range from benign but targeted advertising to more sinister issues like government censorship or cybercriminals tracking your online habits.
DoT and DoH for DNS Privacy
Enter the superheroes of DNS privacy: DNS over TLS (DoT) and DNS over HTTPS (DoH). These protocols are the digital equivalent of putting our postcards in envelopes, shielding our queries from those who might want to sneak a peek.
DoT takes our DNS queries and wraps them in the security of TLS (Transport Layer Security), the same protocol that HTTPS websites use to keep your data safe. When a device initiates a DNS query, it establishes a secure connection with the DNS server through a TLS handshake, ensuring the confidentiality and integrity of the exchange. DoT prevents eavesdropping by encrypting the data, making it indecipherable to unauthorized parties.
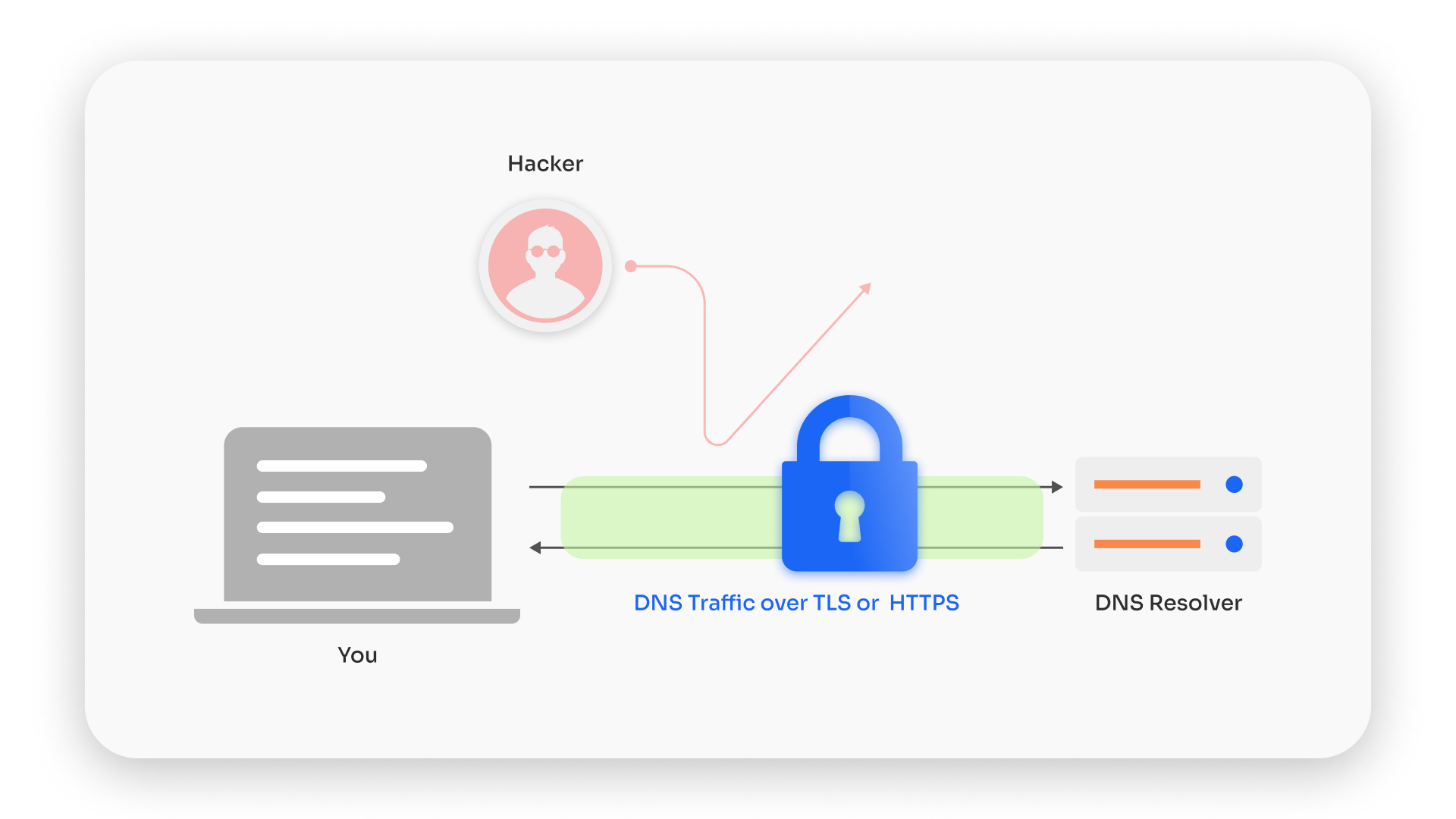
It is like sending your DNS queries in an armored van, ensuring they reach their destination without interference. However, DoT operates on a dedicated port (853), any user with access to the network can see DoT traffic in and out, even if no one can see inside since if the requests and responses themselves are encrypted.
On the flip side, DoH sends these encrypted DNS queries over HTTP or HTTP/2. This means they travel on the same roads as regular internet traffic (port 443), blending in with the crowd. DoH allows users to bypass network restrictions and censorship, making it difficult for intermediaries to selectively inspect or manipulate DNS queries. To a network observer, DoH traffic is indistinguishable from any other secure website visit, making it a master of disguise.
Both DoT and DoH serve the same noble purpose: to protect the privacy and integrity of your DNS queries. They ensure that no one can tamper with or spy on your internet navigation. Yet, their distinct paths—DoT with its exclusive route and DoH camouflaged among the masses—offer different advantages depending on what level of privacy, security measures and compatibility you seek.
SafeDNS also provides the DoT feature, complementing the DoH (DNS over HTTPS) support that is typically enabled by default in most browsers. For guidance on activating DoT through the SafeDNS dashboard, please refer to our detailed instructions available here.
As we stand at this crossroads, the question is not just about which protocol to choose. It is about recognizing the importance of DNS privacy and taking steps to protect it. Whether you lean towards the visibility and security of DoT or the stealth and integration of DoH, the crucial thing is to be aware of your choices and their implications.
In the grand tapestry of the internet, where every click, search, and query weaves a thread, ensuring these threads are secure and private is vital. It is about more than just safeguarding data; it is about preserving the freedom and trust that lie at the heart of the digital age. As we continue to navigate this ever-changing landscape, let us do so with an eye towards not just where we are going, but how safely and privately we can get there.
Take advantage of the SafeDNS trial period and try all the best features

