
DNS Tunneling: An Overview of Cybersecurity Risks
Amidst the ever-changing landscape of cybersecurity, new threats continue to emerge, and among them lies the covert menace of DNS tunneling. This elusive technique enables cybercriminals to exploit the Domain Name System, covertly transferring data without detection.
What is DNS Tunneling?
DNS tunneling is a sophisticated cybersecurity technique that enables attackers to establish covert communication channels by utilizing the DNS protocol, which was originally designed for translating domain names into IP addresses. In a typical DNS transaction, a user's device sends a query to a DNS resolver, which then returns the corresponding IP address. However, malicious actors exploit this communication process to hide and transport unauthorized data within DNS queries and responses.
This method of data exfiltration and communication poses a significant threat to network security, as it allows attackers to bypass traditional security mechanisms, such as firewalls and proxies, that usually monitor and filter internet traffic based on standard protocols. As a result, DNS tunneling becomes a preferred choice for cybercriminals seeking to remain undetected while transferring sensitive information or controlling compromised systems.
How Does DNS Tunneling Work?
DNS tunneling works by infiltrating a malware command and control (C&C) server into the network, which then sends DNS requests to external malware-controlled servers. These servers resolve the DNS queries to reveal and communicate additional information, usually in the form of a hidden payload.
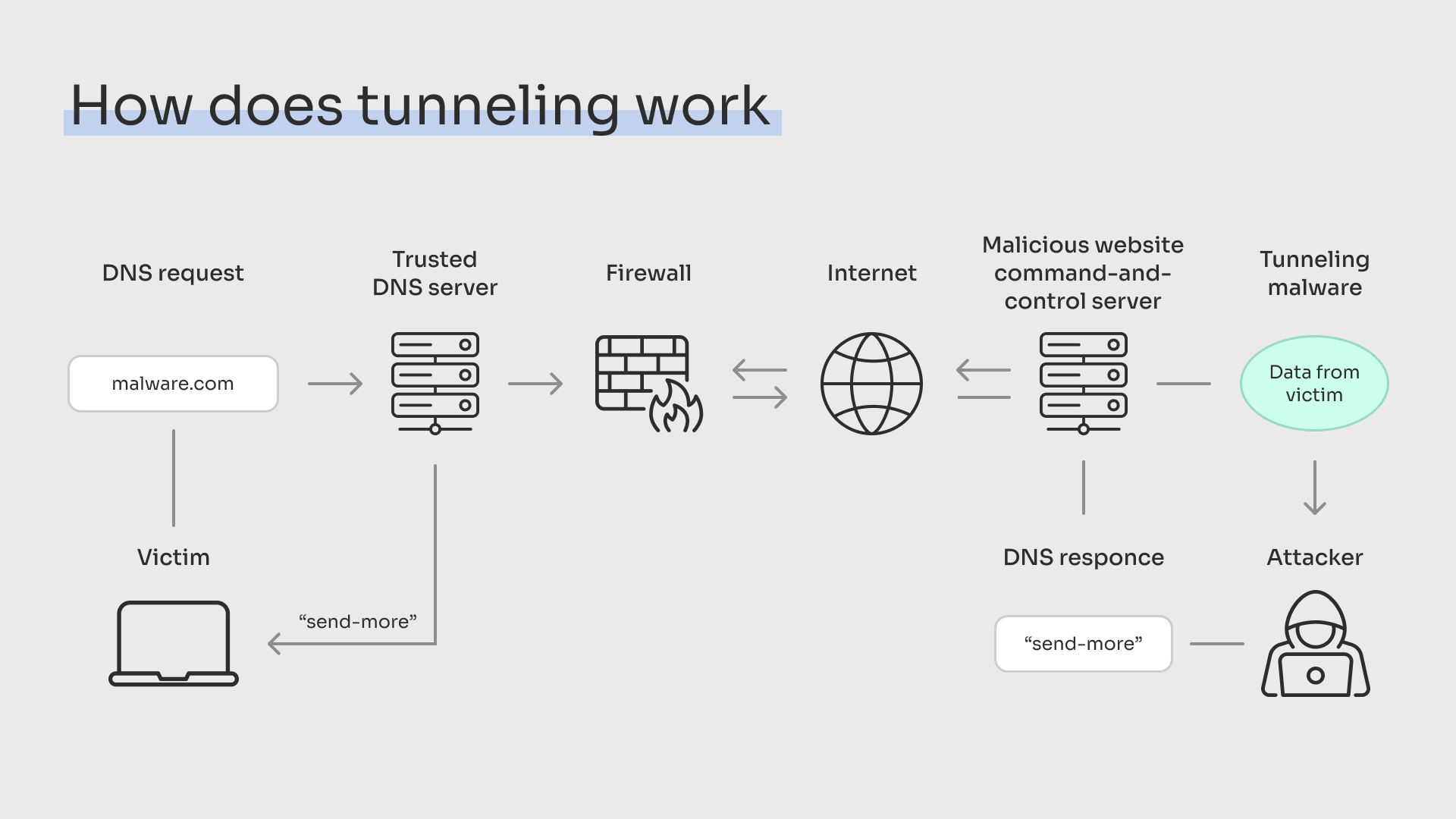
The malware can then hide its activities in these DNS requests and responses since they are often overlooked by firewalls. The hackers can then use the incoming DNS queries to extract data from the network and covertly transmit the payloads to a remote C&C server.
DNS tunneling is a dangerous tactic that malicious actors can use to bypass standard security measures. In this attack, an attacker will infiltrate an internal DNS server and send DNS requests to an external target DNS server. The internal DNS server will then send the request to the target DNS server, which will resolve it and return additional information in the form.
Risks Associated with DNS Tunneling
DNS tunneling poses severe risks to organizations. One of the most significant dangers is that it can allow cybercriminals to bypass firewalls and other security protocols.
It can also lead to the theft of sensitive information, such as confidential business data and personal customer information, that might be encrypted or not secured correctly, opening up the possibility for it to be exfiltrated from the network.
Moreover, DNS tunneling can make it particularly challenging for IT teams to detect and prevent attacks from taking place because the attack traffic typically uses the same protocol that the organization uses for its everyday operations.
DNS tunneling attacks have been used to great effect by malicious actors in the real world, leading to significant damage to industries and organizations.
In 2019, researchers discovered a DNS tunneling attack targeting a large international energy company. In this case, attackers managed to gain access to the company’s internal network via a compromised domain name system server. After gaining access, they used DNS tunneling techniques to send malicious payloads into the network that allowed them to exfiltrate sensitive data.
In 2020, an attacker targeted an Australian logistics firm with a DNS tunneling attack, resulting in the theft of confidential business information and customer data. The attacker was able to bypass security protocols by sending out malicious requests hidden in standard DNS queries.
DNS tunneling attacks can also be used as part of more sophisticated campaigns. In one instance, attackers created a fake domain name system server that they then used to launch distributed denial-of-service (DDoS) attacks against multiple organizations simultaneously. By hiding their traffic in DNS queries, they were able to use their own fake server as the source of the attack without detection.
DNS tunneling is a particularly dangerous type of cyberattack that has caused significant damage to various industries and organizations around the world. It allows attackers to bypass standard security measures and exfiltrate sensitive data from networks undetected. As such, it is important for organizations and businesses alike to remain vigilant against this form of attack and take steps towards mitigating its risk whenever possible.
Recognizing DNS Tunneling
DNS tunneling can be difficult to spot due to the fact that it uses the same protocol as other network activities, making it hard to differentiate malicious traffic from legitimate traffic.
However, there are a few signs that IT professionals can look for when attempting to recognize DNS tunneling. For example, if an internal server is sending requests or receiving data from strange IP addresses, this could be a sign of DNS tunneling. Additionally, spikes in DNS query volume or unusually high amounts of traffic coming from a particular domain name could indicate malicious activity.
Other indicators of DNS tunneling include unusual port connections and unencrypted data being sent over the network. Monitoring services such as netflow and packet capture can help businesses detect these suspicious patterns and alert them of any potential threats.
Organizations should also look out for any anomalous behavior from trusted users; while most users will only use standard DNS protocol commands, any sudden changes or unfamiliar commands could signify malicious intent. In addition, Domain Name System Security Extensions (DNSSEC) should be enabled on all systems to prevent attackers from manipulating records and bypassing security protocols.
How to Protect Against DNS Tunneling
To avoid falling victim to DNS tunneling, it is crucial to have a multi-layered approach to cyber defense in your organization.
Secondly, keep all your software updated and apply strict patch management practices. Ensure that DNS servers are patched and kept up-to-date with the latest security standards, which can help fix vulnerabilities.
Finally, establish security protocols for your users, including access policies, credentials, and dynamic passwords across your network.
Conclusion
DNS tunneling poses significant threats to organizations. Preventing these attacks requires a multi-layered approach to network security to ensure all potential exploits and system vulnerabilities are detected and prevented. From protective firewalls to critical system processes implementation, there is much that companies can do to protect themselves against DNS tunneling attacks and other similar cybersecurity threats. Employing proper security measures, IT teams can shrug off network vulnerabilities.
Take advantage of the SafeDNS trial period and try all the best features

