
DNS Poisoning: Understanding the Threat and Securing Your Online Experience
In the world of the Internet, the Domain Name System (DNS) plays a vital role in translating human-readable website addresses into computer-readable IP addresses. It acts as a directory that helps users navigate the vast online landscape. However, the DNS is not immune to security threats, and one such threat is DNS poisoning. In this blog post, we will delve into the intricacies of DNS poisoning, its potential dangers to internet users, and how SafeDNS can protect your online activities. Let's explore this topic further.
What is DNS Poisoning?
DNS poisoning, also known as DNS cache poisoning or DNS spoofing, is a cyber attack that manipulates the DNS resolution process to redirect users to malicious websites or intercept their network traffic. This attack targets the DNS cache, where previously resolved domain names and their corresponding IP addresses are stored. By injecting false information into the DNS cache, attackers can trick users and redirect online traffic from them to malicious websites without their knowledge or consent.
Attackers can poison DNS caches by impersonating DNS name servers, making a request to a DNS resolver and then spoofing the response when the DNS resolver queries a name server. This is possible because DNS servers use UDP (User Datagram Protocol) instead of TCP and because there is currently no verification of DNS information.
The Mechanics of DNS Poisoning
DNS poisoning typically occurs in two forms: client-side and server-side attacks. In a client-side DNS poisoning attack, malware infects the user's device and modifies its DNS settings to redirect DNS requests to malicious servers. On the other hand, server-side attacks exploit vulnerabilities in DNS servers, allowing attackers to inject false DNS records directly into the server's cache. This enables them to redirect traffic across multiple devices connected to the compromised server.
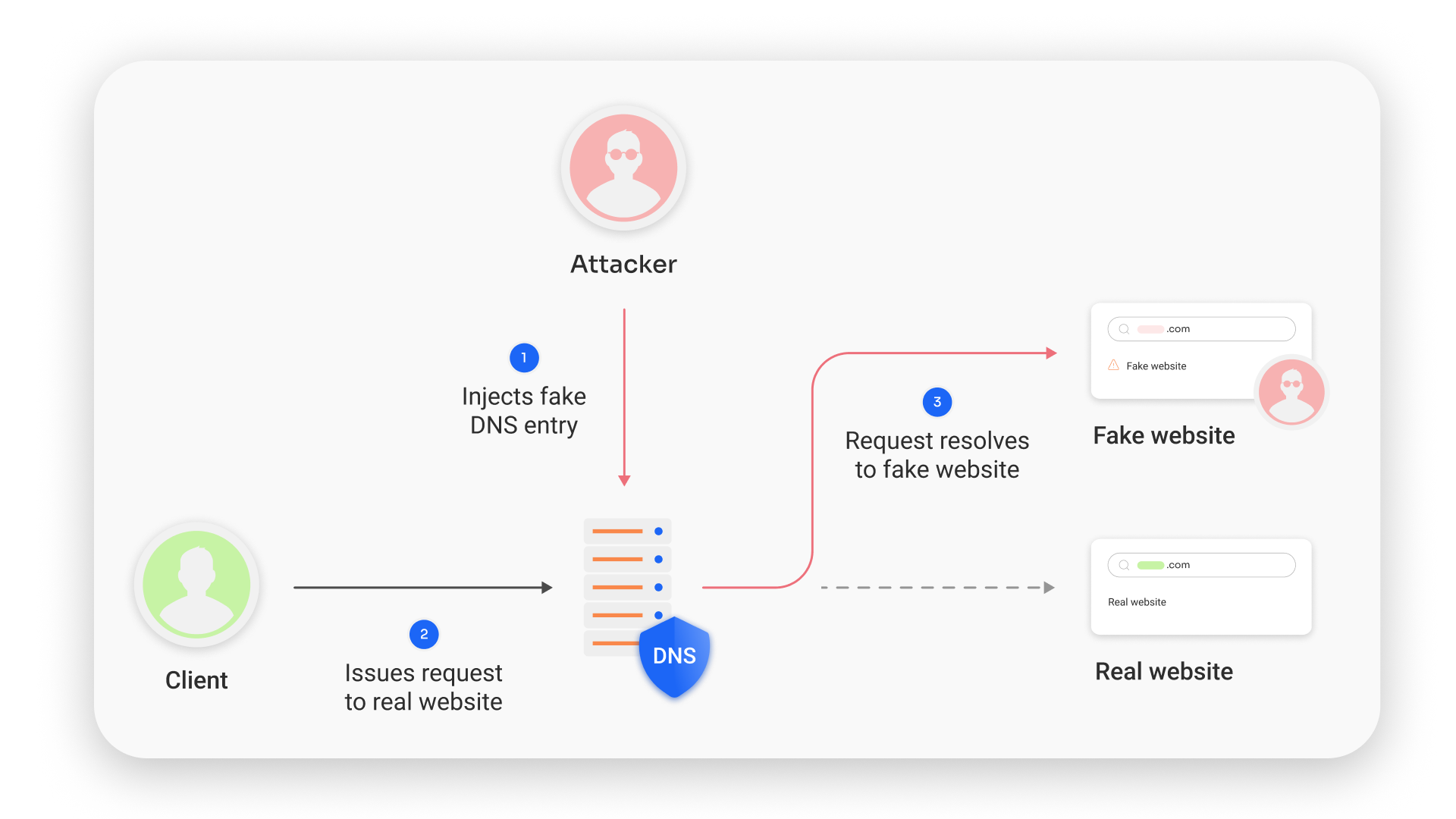
The Dangers of DNS Poisoning
DNS poisoning can have severe consequences for both individuals and organizations. Here are a few notable dangers:
- Leakage of Sensitive Data: Phishing attacks can lead to the leakage of sensitive data. Attackers may attempt to trick users into revealing confidential information such as bank card details, login credentials, or personal information. By impersonating legitimate websites or services, phishing attacks can result in the inadvertent disclosure of sensitive data to malicious actors.
- Malware Distribution: DNS poisoning can be employed to redirect users to websites that host malware, resulting in unintended downloads and installations of malicious software.
- Unauthorized Data Access: Man-in-the-Middle attacks pose the risk of unauthorized access to personal data or the interception of sensitive information. In such attacks, malicious actors can intercept network traffic and manipulate or steal data by altering packets. This can lead to the exposure of personal information, financial data, or the reception of misleading and untrustworthy information.
- Brand Reputation Damage: Organizations may face reputational damage if their customers unknowingly access malicious websites that imitate their legitimate platforms, leading to compromised data or financial losses.
Detecting and Mitigating DNS Poisoning Attacks
Detecting and mitigating DNS spoofing attacks is crucial to ensuring online security. While there are various security solutions available, it is essential to understand the techniques and best practices that can help identify and counter DNS poisoning attacks. Here are some effective strategies:
- DNSSEC Implementation: DNS Security Extensions (DNSSEC) is a security protocol that adds an extra layer of authentication to DNS responses. By digitally signing DNS records, DNSSEC prevents attackers from injecting false information into the DNS cache and helps validate the authenticity of DNS responses.
- Regular DNS Monitoring: Organizations should proactively monitor their DNS infrastructure for any signs of poisoning attacks. This involves analyzing DNS traffic patterns, monitoring DNS cache contents, and utilizing intrusion detection systems (IDS) or security information and event management (SIEM) solutions to identify suspicious activities.
- DNS Firewall Protection: Deploying a DNS firewall can help block malicious DNS requests and prevent DNS poisoning of caches. DNS firewalls use threat intelligence, reputation-based filtering, and behavioral analysis to identify and block DNS requests associated with known malicious domains or suspicious behavior.
- Encrypted DNS (DoT/DoH): Encrypted DNS protocols such as DNS over TLS (DoT) and DNS over HTTPS (DoH) provide an additional layer of security by encrypting DNS traffic between clients and DNS resolvers. This prevents attackers from eavesdropping on or tampering with DNS requests and responses.
- Regular Security Audits: Conducting regular security audits of DNS infrastructure helps identify vulnerabilities and ensure proper configuration. This includes reviewing DNS server settings, access controls, and applying necessary patches and updates to mitigate potential security risks.
By implementing these strategies and staying vigilant, organizations can significantly reduce the risk of DNS poisoning attacks and protect their online presence and sensitive information.
Safeguarding DNS Infrastructure with Secure Practices
In addition to specific techniques for detecting and mitigating DNS poisoning attacks, there are general best practices to safeguard DNS infrastructure. Consider the following security protocols.
- Implement Access Controls: Restrict access to DNS servers by allowing only authorized personnel to make changes to DNS configurations. Enforce strong authentication measures, including two-factor authentication (2FA) or multi-factor authentication (MFA).
- Regularly Patch and Update: Keep DNS servers and associated software up to date with the latest security patches and updates. Promptly address any known vulnerabilities to minimize the risk of exploitation.
- Employ Network Segmentation: Separate DNS servers from other critical infrastructure by implementing network segmentation. This prevents unauthorized access or lateral movement in case of a security breach.
- Backup and Recovery: Regularly backup DNS configurations and zone files. In the event of a DNS cache poisoning attack, having recent backups ensures quick recovery and reduces the impact on DNS services.
- Continuous Staff Training: Provide ongoing training to IT staff and employees to educate them about DNS poisoning attacks, phishing techniques, and general cybersecurity practices. Encourage reporting of suspicious activities to facilitate early detection and response. Consider SafeDNS cybersecurity awareness training to equip employees with the knowledge and skills needed to identify and respond to potential security risks.
Conclusion
DNS poisoning attacks pose a significant threat to online security, but with the right strategies and practices in place, organizations can detect and mitigate these attacks effectively. By implementing DNSSEC, monitoring DNS traffic, utilizing DNS firewalls, and practicing secure DNS infrastructure management, organizations can safeguard their online presence and protect sensitive information. Employing these techniques, along with regular security audits and staff training, will contribute to a robust defense against DNS poisoning attacks.
Take advantage of the SafeDNS trial period and try all the best features

