The Battle Against Domain Generation Algorithms
The Internet has become something like the very air we breathe, ensuring its safety is paramount. Yet, lurking within this indispensable resource is a sophisticated threat known as Domain Generation Algorithms (DGA). But what exactly is a Domain Generation Algorithm (DGA), and why is it a topic of concern for cybersecurity teams and everyday internet users alike? Let's embark on a journey to demystify DGA, its implications, its threat actors and the innovative measures being taken to combat it.
How DGAs Operate
Consider a machine infected with a botnet, like a sleeper agent awaiting orders. If this agent's meeting point is compromised, they can no longer receive commands, rendering them ineffective. It resembles knowing exactly where a spy is going to drop their secrets. Once that location is discovered and watched, the spy's effectiveness is nullified. Hence, the logic behind DGAs: never stick to one domain. By constantly changing domains based on a specific algorithm, these digital spies stay one step ahead, making it challenging for cybersecurity teams to catch them.
The Challenge of Detection: Separating Wheat from Chaff
Yet, the task of detecting malicious domains generated by these algorithms is not as daunting as one might think. The real challenge lies in distinguishing between DGA-generated domains and legitimate technical domains. It looks like trying to find a needle in a haystack, except some of the needles look remarkably similar to the hay. For example, Microsoft's technical domains could easily be mistaken for those generated by DGAs, leading to a plethora of false positives. It's a fine line to walk, requiring not just technical prowess but also a deep understanding of both legitimate domains and malicious digital behaviors.
The role of DGA in cybersecurity
The Domain Generation Algorithm (DGA) has been a big deal in malware for the past ten years. It's crucial to understand how DGA attacks work to keep your network safe from malware. Security software can quickly block malware that depends on a fixed domain or static IP addresses. Essentially, cyber attackers use DGAs to constantly create malicious domains and IP addresses for their malware's control servers. This makes it hard for defenders to catch them because they keep changing domains. Even though DGAs have been around for a while, security researchers say they're still tough to deal with. But new technologies are being developed to tackle them better.
DGAs have been a headache for malware victims for over a decade. Big malware attacks like Conficker, Zeus, and Dyre have used DGAs to keep changing domains and their control servers' addresses. Normal security software can't keep up because the malware keeps switching domains. But now, new technologies that use big data and machine learning are being developed to predict and stop these attacks before they happen. They aim to make it harder for attackers to set up malicious sites in the same domain names in first place.
SafeDNS's Strategies Against Domain Generation Algorithms
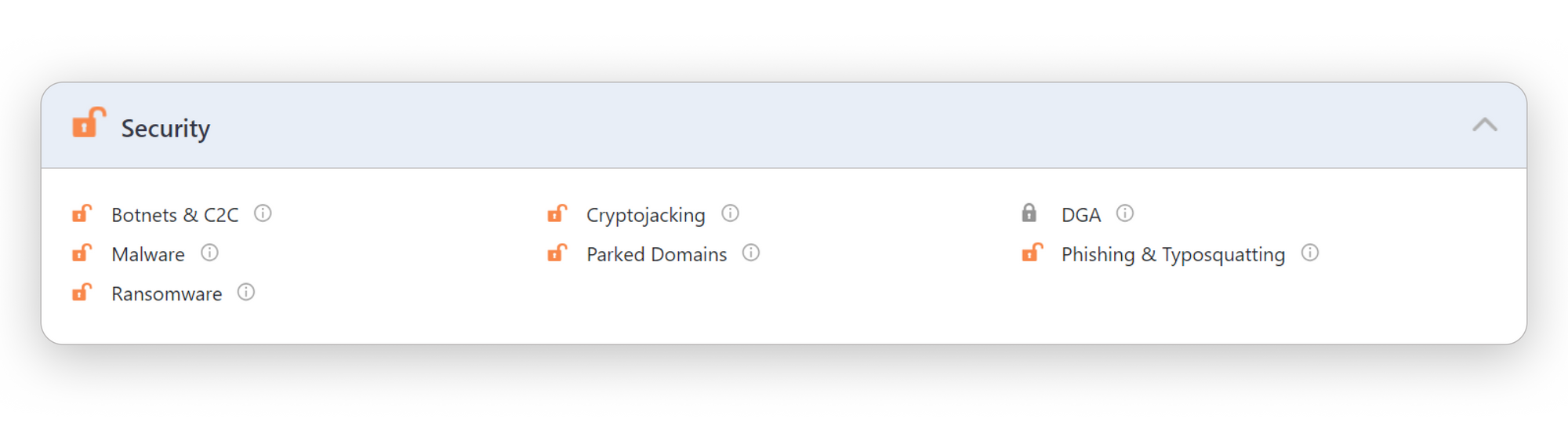
In response to this challenge, SafeDNS has pioneered an approach by creating a separate category for DGA domains. This initiative is not just about enhancing cybersecurity measures; it is about adapting to modern digital threats. DGA is not limited to shadowy corners of the internet; it is actively used by a wide array of platforms, including numerous gambling sites. Take 1xBet, for instance. This application leverages automatically generated domains to ensure its continuous operation, making it a tough nut to crack for those looking to block it. However, the domainexperts at SafeDNS are not easily outmaneuvered. Through meticulous analysis of application traffic and the intricate web of connections between servers, IP addresses, and generated domains, our experts manage to detect about 10 new domains daily for only this particular application, blocking them effectively and safeguarding users.
The Widespread Use of a Domain Generation Algorithm (DGA)
The use of DGA extends far beyond gambling platforms, playing a crucial role in the operation of botnets and corresponding cyberattacks. These automatically generated domains can be employed for a variety of purposes, ranging from benign technical needs to more nefarious activities. It underscores a fundamental truth about the digital age: the tools and technologies developed can serve both to advance and to undermine our collective security.
So, what does this all mean for the average internet user and for organizations striving to protect their networks? It highlights the need for constant vigilance, innovation, and adaptation. The creation of a separate category for DGA domains by SafeDNS is a testament to the proactive stance required to stay ahead of cybercriminals.
But let's pause for a moment to ask ourselves a question: In the grand scheme of things, what can we, as individuals and as a community, do to contribute to the safety and security of our digital world? It begins with awareness of cyber attacks, understanding the nature of threats like DGA, and supporting the efforts of cybersecurity professionals. By staying informed about security solutions and adopting safe online practices, we play a part in this vast ecosystem, helping to safeguard not just our own digital footprint but also contributing to the broader effort to secure the internet for everyone.
The story of DGA is a fascinating glimpse into the ongoing struggle between cybercriminals and cybersecurity experts. It is a reminder that adaptation and resilience are key to overcoming challenges. SafeDNS's innovative approach to tackling DGA-generated domains exemplifies the kind of forward-thinking strategy that will define the future of cybersecurity. As we continue to deal with the complexities of the internet, let’s do so with a commitment to safety, security, and the collective well-being of our networks.
Take advantage of the SafeDNS trial period and try all the best features

